Securing s3-website
Launching the CloudFormation template in the previous post will create our s3-website, however it will not be available over HTTPS. Out of the box there are some limitations with s3-website relating to serving secure content.
- The Route53 record directs to an endpoint hosted by AWS, for example in eu-west-1 the endpoint is s3-website-eu-west-1.amazonaws.com. This endpoint does not accept HTTPS connections.
- Even if the endpoint did accept HTTPS connections the visitors web browser would return a certificate mismatch error. The user visiting your website address (example.com) would be presented a certificate for s3-website-eu-west-1.amazonaws.com.
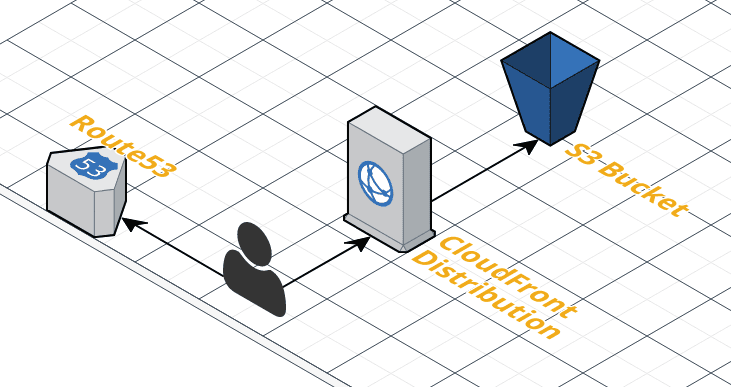
In order to serve secure content a CloudFront Distribution must be placed in-front of the S3 bucket containing your content.
Adding in CloudFront
CloudFront is AWS’s global Content Distribution Network (CDN) product. S3 is capable of serve the website around the world however only from one AWS Region. CloudFront is able to serve content from multiple geographic locations meaning faster response times for website visitors around the world.
It also helps to resolve the HTTPS limitations with S3-Website.
CloudFront can be highly customised and is a complicated product. The use case for this website is fairly simple. Our CloudFront setup has the following attributes:
- The Origin is the source of content to serve through the Distribution and is set to the s3 bucket created previously holding website content. (The s3-website limitation whereby the bucket name must match the custom domain name no longer applies, the bucket can be given any name).
- Insecure (http) requests are redirected to secure (https) automatically.
- Content is served only in US, Canada and Europe to control costs.
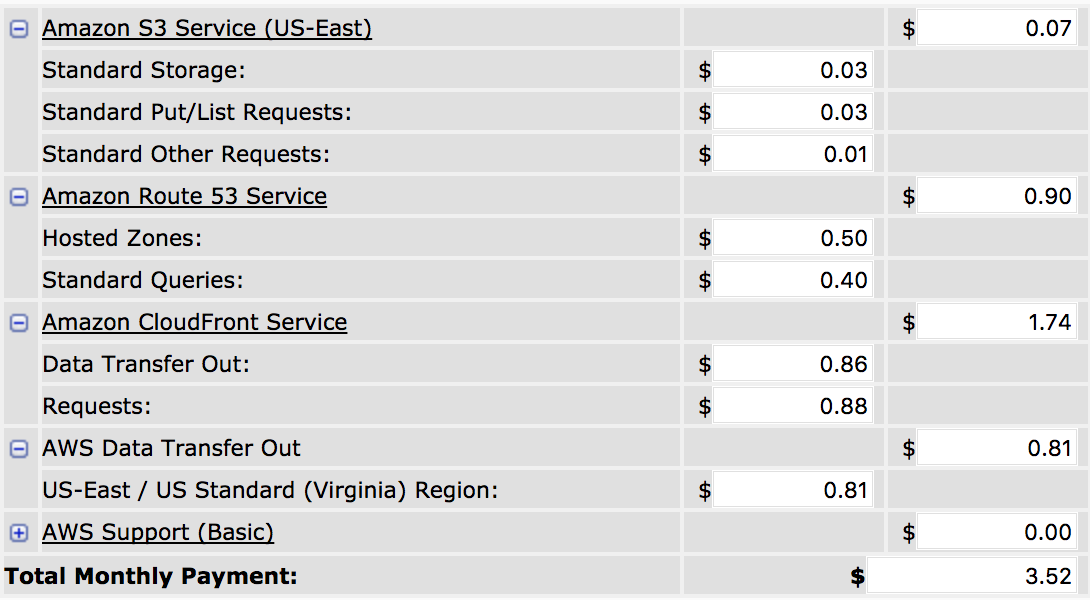
Adding in CloudFront barely has any impact on pricing. A very rough price estimate including 1GB of storage and 10GB monthly data transfer yields a monthly cost of $3.50.
The CloudFormation template
See the next article in this series: CloudFormation template for a CloudFront enabled S3-Website